As we know, Data link layer is responsible for movements of the frames from one hop to the next (hop-to-hop delivery).
There are mainly two functions of data link layer: data link control and media access control.
Data link control
It includes framing, flow control and error control and some software based protocols that provide easy ad reliable transmission of frames between hops.
Framing
Like we know, physical layer in network models is concerned with the movements of the bits in the form of signal from a source to destination.
But on the other hand, data link layer needs to bundle those bits into frames, so that each frames can be differentiated from another.
Framing separates a message from one source to a destination by adding a sender address and a destination address. Sender address contains the address of the recipient (to acknowledge the receipt) and destination address contains where the packet needs to go.
Two types of approach are in hand for framing,
a) Character-Oriented approach.
b) Bit-Oriented approach.
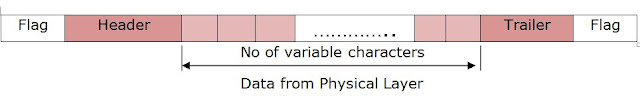
Character-Oriented protocol: In a character oriented protocol, 8-bit character data is to be carried from a coding system such as ASCII. The header contains the source and destination address and other information, the trailer contains error detection or error correction redundant bits, which are also multiples of 8 bit.
To separate one frame from the next, a 1 Byte (8 bit) flag is added at the beginning and at the end of the frame.
Look at the picture below for better understanding,
The character oriented framing was used only for text communication by data link layers. The flag could be selected to be any character not used for text communication.
However, nowadays we can send graphs, audio, and video as well. Any pattern used for the flag could also be a part of the information. But whenever this happens, the receiver when it encounters this pattern in the middle of the data, thinks it has reached the end the frame. And hence, it became a serious problem to be dealt on.
This problem was fixed by using byte stuffingstrategy.
In byte stuffing, a special byte (character) known as Escape character (ESC) is added to the data section of the frame when there is a character with same the pattern as the flag. Thus, the data section is stuffed with an extra byte.
In this case, whenever the receiver encounters an ESC character, it removes the ESC from the data section and treats the next character as data, not a flag.
Note: Byte staffing is just a process of adding 1 extra byte whenever there’s a flag or escape character in the text.
Bit-Oriented protocol: In this case, the data section in the frame is a sequence of bits to be interpreted by the upper layer as audio, video and text etc. Nevertheless, in addition to headers and trailers we need to have a delimiter to separate from one frame to another. Here, we use a 8-bit pattern flag such as ‘01111110’ as the delimiter to recognize the beginning and the end of the frame.
However, this flag can create same type of problem occurred in character-oriented protocol.
So, what do we do?
We, do this by staffing 1 single bit (instead of 1 byte) to put a stop to the pattern looking like a flag. This is called bit staffing.
In bit staffing, if a 0 and five consecutive 1 bits are encountered, we add an extra 0 over there. This extra 0 is eventually removed from the data received by the receiver. This guarantees that the flag field sequence does not appear in the frame.
Look at the picture below,
STUDY SESSIONS
Q1: What is Framing? and what are their approach?
Q2. What is Character-based approach? what is the problem associated with it, and how it is solved?
Q3. What is bit-oriented approach? what is the problem associated with it, and how it is solved?
PLEASE USE THE COMMENT SECTION FOR ANY DOUBTS AND QUARIES.





0 Comments